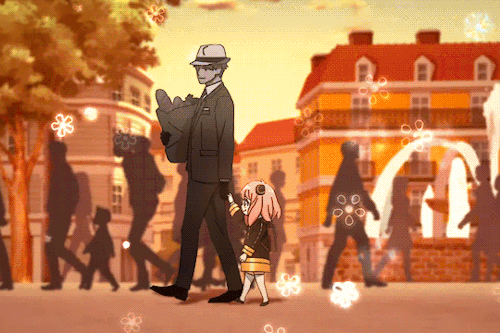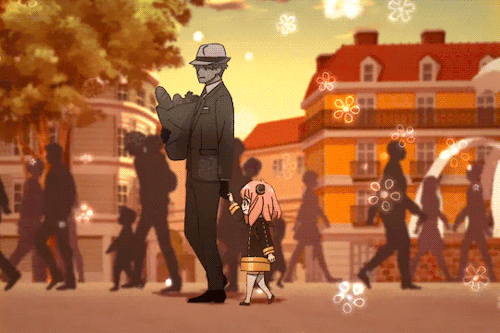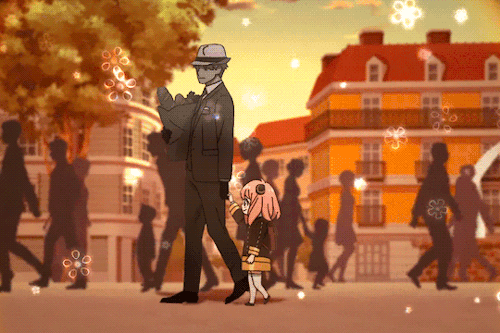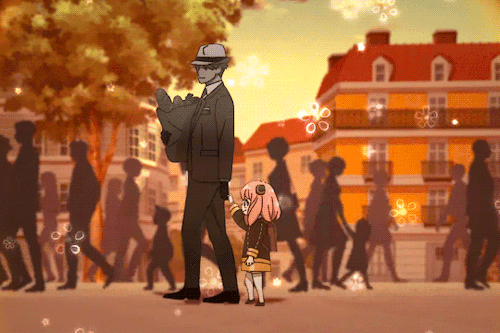
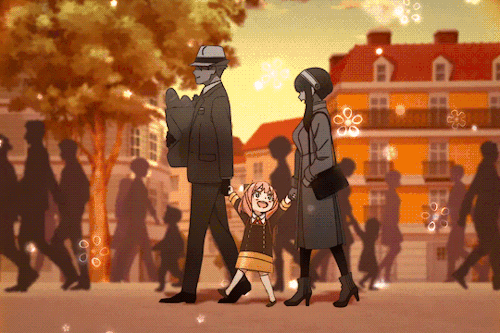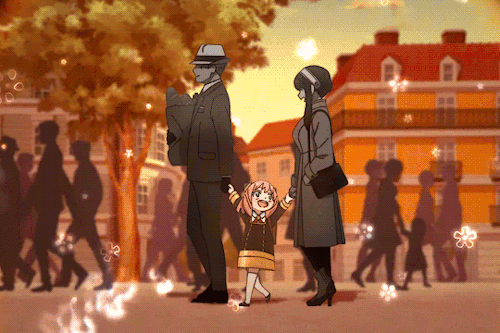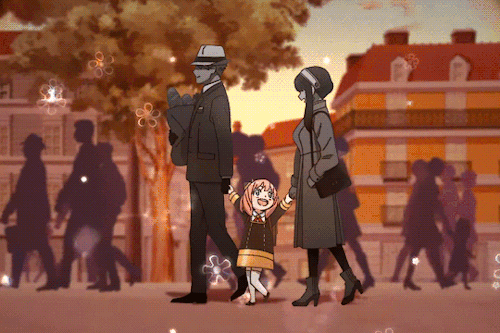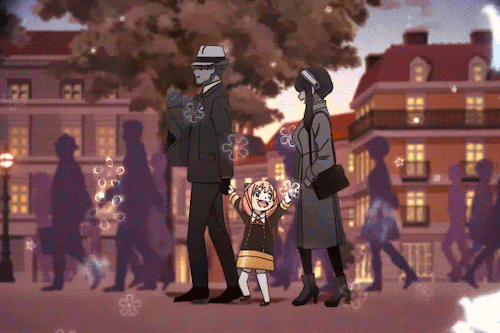
If You’re Having A Bad Day, Here’s A Cute Little Marching Band
if you’re having a bad day, here’s a cute little marching band
More Posts from Thatlethargicsmile and Others
Everyone wants toxic yuri and complex female characters until the yuri is toxic and the female characters are complex :(
On one hand, I am loathe to spend money on something as fleeting and useless as a tumblr post. On the other hand, I want to make everyone look at this picture of my cat:

Don't think I've seen them all together in one big video like this before
and it is of course well known that dragons are very cutes
dead wife who was MEAN and slept without a TOP SHEET and only went to the beach when it was OVERCAST to SCOWL at the waves


Inspired by that opening everyone likes
Girl you need to get out of bed faster than this

Never ever turn off your phone: rethinking security culture in the era of big data analysis.
Back in the 80′s if you were a pissed off anarchist that wanted to burn down a building, you probably checked your home for listening devices and made a plan. If you were the same kind of pissed off anarchist in the late 90′s, you turned off your phone and encrypted your online traffic. In the 2020′s we’re gonna have to change our strategies once again. Intelligence gathering has adapted and so we must adapt too.
To get a head start at this, let’s look at how big data analysis is being used. To do this, we’ll need to talk about 3 things: metadata, patterns and networks. Those sound boring and complicated but I’m not a techy and I won’t bore you with tech language, I’ll keep it as easy as I can.
Metadata: In the context of online activity, ‘content’ means ‘the message you send’ and ‘metadata’ means ‘everything other than the content’. So, for example, if you send your friend a text about lunch, the content might be “Let’s go out for lunch” and the metadata might be “Message send at 01/04/2018 11.32 from phone 0478239055 to phone 079726823 using Signal”.
This information is registered by your phone even if the app encrypts your actual message. Your metadata is very badly protected by technology and very badly protected by the law. No matter which country you are in, most of your metadata if freely available to intelligence agencies regardless of whether you are a suspect in anything.
Patterns: Whether you realize it or not, your metadata has a pattern. If you have a daily job you might have a very consistent pattern, if you do not your pattern might be more flexible but you have a pattern. If someone wanted to know the rhythm of your day, they could very easily do so because your pattern is in the metadata.
For example: Maybe you use the wifi at your favourite bar on most Sunday nights until about midnight, you wake up around 10 AM and check your Signal, you use your public transport card to get to class every Monday afternoon and you spend on average 1 hour on Tumblr twice a day. All this is part of your pattern.
Networks: You have online networks. Your facebook friends, the people in your phone adress book, the dropbox you share with coworkers, everyone who bought online tickets to the same punk band you attended, the people using the same wifi points as you. Take your networks, combine them with other people’s networks, and clusters reveal themselves. Your work community, your family, your activist scene, etc.
If you are in an anarchist community that will probably be abundantly clear from all your minor network connections like going to the same band and knowing the same people as other anarchists. Even if you never liked an anarchist facebook page or pressed ‘going’ on an anarchist facebook event, your network is hard to hide.
Now, let’s say you commit a crime,
the kind that would result in some serious research. Let’s say that on Sunday night 3 AM, you are your friends go out and burn down a nazi’s house. (Of course I would never advice any of you to do such a thing.) It’s obvious that anarchists did it but there are no other clues. You use traditional style security culture: you burn your notes, you are careful not to communicate about your plans near technology and you do not leave physical traces.
But because you commited the crime that night, your metadata will vary strongly from your usual rhythm: you stay at your usual bar until 2 AM to wait for your friends, you do not wake up at 10 AM in the morning so you do not check your Signal or Tumblr until 1 PM. You do not go to class. Your metadata pattern is very different from your usual pattern. The metadata patterns of your friends are different too. If one of you is clumsy, they might generate a super suspicious metadata signal like a phone being switched off at 2.30 AM and activated at 4AM. You wouldn’t be the first.
If I wanted to solve this crime using data analysis, what I would do is:
let a piece of software run a pattern analysis of the local anarchist scene to generate the 300 people most connected to the anarchist scene.
let a second piece of software analyse the metadata patterns of those 300 people over the last months and identify the biggest metadata variations around Sunday night as well as very suspicious metadata activity
Illiminate pattern variations with an obvious cause or an obvious alibi (people who are on vacation, people who are in the hospital, people who lost their job, etc).
Do indepth research into the ones that remain.
Which is how, out of a massive amount of people that I couldn’t possible all listen to at the same time, I could quickly identify a few to monitor closely. This is how I could find and catch you.
So, now what?
If traditional security culture doesn’t protect us as well as it used to, how do we adapt? Well, I don’t have all the answers but for a start, I’d say: know your network + know your pattern.
In the case of the example above: leave the bar at midnight, return home and put your phone on your bedside table. Check the apps you check before going to bed and set your alarm to 10AM. Return to the bar without your phone. Wake up at 10AM and check your Signal. Drag yourself to class or ask a comrade to make the trip with your travel card and do not use technology in your home while the comrade is taking your travel card to class. Stick to your pattern. Never ever turn off your phone.
You might also be able to manipulate your network but that seems much harder to do. Not having a smartphone and dropping out of all social activity online is a big commitment. Knowing your data pattern and making sure your data pattern doesn’t look out of the ordinary? Much less commitment.
Some of the old rules will still apply: don’t talk about a crime around devices with microphones, don’t brag after a succesful action, etc. Other rules, like ‘turn off your phone when planning an illegal act’ need to change because their metada looks too out of the ordinary. No one switches off their phone anymore. We look suspicious as fuck when we do.
This is just one idea on how we could update our security culture. There are probably other people with other, better ideas about updating our security culture. If we start the conversation, we may get somewhere.
Finally: we need to keep adapting.
As technology changes, more information is becoming available, including data we have very little control over. Smart-tv’s and ads in public spaces that listen to every word we say and the tone of our voice when we say it are examples. Data analysis projects are currently using license plate reading software on security footage to map the travel patterns of cars. A lot suggests they may soon be ready to do the same with face recognition, at which point the presence of our face in public space becomes part of our metadata. More information means more accurate data analysis. Our metadata may soon be too vast annd too complex to completely map and mirror. Which means we will need to adapt our counter measures if you want to hide something.
How do we keep it all under the radar? I don’t know. But let’s try to figure this shit out. These are some first thoughts about what security culture should look like in the age of modern big data analysis and I’d be very happy for any insights from comrades that have some thoughts on this.
Also: feel free to distribute and rework these words without credit.
-
 lizzie-kin reblogged this · 1 week ago
lizzie-kin reblogged this · 1 week ago -
 caiscagames reblogged this · 1 week ago
caiscagames reblogged this · 1 week ago -
 clarabeau liked this · 1 week ago
clarabeau liked this · 1 week ago -
 mr-top-secret reblogged this · 1 week ago
mr-top-secret reblogged this · 1 week ago -
 flowers10chb reblogged this · 1 week ago
flowers10chb reblogged this · 1 week ago -
 easybreezyscatterbrain liked this · 1 week ago
easybreezyscatterbrain liked this · 1 week ago -
 troacctid reblogged this · 1 week ago
troacctid reblogged this · 1 week ago -
 lost-and-enbious liked this · 1 week ago
lost-and-enbious liked this · 1 week ago -
 ellunete liked this · 1 week ago
ellunete liked this · 1 week ago -
 dhrlove reblogged this · 1 week ago
dhrlove reblogged this · 1 week ago -
 cactusghoti reblogged this · 1 week ago
cactusghoti reblogged this · 1 week ago -
 thevoidwatches reblogged this · 1 week ago
thevoidwatches reblogged this · 1 week ago -
 whythursdaynext reblogged this · 1 week ago
whythursdaynext reblogged this · 1 week ago -
 quipxotic liked this · 1 week ago
quipxotic liked this · 1 week ago -
 taavicleric reblogged this · 1 week ago
taavicleric reblogged this · 1 week ago -
 lubsnubsbubs reblogged this · 1 week ago
lubsnubsbubs reblogged this · 1 week ago -
 teacat12 reblogged this · 1 week ago
teacat12 reblogged this · 1 week ago -
 grturtsu6t liked this · 1 week ago
grturtsu6t liked this · 1 week ago -
 fancytaiyaki liked this · 1 week ago
fancytaiyaki liked this · 1 week ago -
 watchtimeticktock reblogged this · 1 week ago
watchtimeticktock reblogged this · 1 week ago -
 watchtimeticktock liked this · 1 week ago
watchtimeticktock liked this · 1 week ago -
 thestorycontinues reblogged this · 1 week ago
thestorycontinues reblogged this · 1 week ago -
 fresastar liked this · 1 week ago
fresastar liked this · 1 week ago -
 thelittle-light liked this · 1 week ago
thelittle-light liked this · 1 week ago -
 thecozynerd liked this · 1 week ago
thecozynerd liked this · 1 week ago -
 skeecil liked this · 2 weeks ago
skeecil liked this · 2 weeks ago -
 luxaii reblogged this · 2 weeks ago
luxaii reblogged this · 2 weeks ago -
 heart-devouring-crocodilian liked this · 2 weeks ago
heart-devouring-crocodilian liked this · 2 weeks ago -
 fluffball19 liked this · 2 weeks ago
fluffball19 liked this · 2 weeks ago -
 thebirdfantasy liked this · 2 weeks ago
thebirdfantasy liked this · 2 weeks ago -
 copperzealot reblogged this · 2 weeks ago
copperzealot reblogged this · 2 weeks ago -
 mulberryhill reblogged this · 2 weeks ago
mulberryhill reblogged this · 2 weeks ago -
 mulberryhill liked this · 2 weeks ago
mulberryhill liked this · 2 weeks ago -
 kammie16 liked this · 2 weeks ago
kammie16 liked this · 2 weeks ago -
 foxwithabunnyhoard reblogged this · 2 weeks ago
foxwithabunnyhoard reblogged this · 2 weeks ago -
 slightysquishycheese reblogged this · 2 weeks ago
slightysquishycheese reblogged this · 2 weeks ago -
 dr-archeville liked this · 2 weeks ago
dr-archeville liked this · 2 weeks ago -
 slightysquishycheese liked this · 2 weeks ago
slightysquishycheese liked this · 2 weeks ago -
 missimbalance reblogged this · 2 weeks ago
missimbalance reblogged this · 2 weeks ago -
 boahamcock reblogged this · 2 weeks ago
boahamcock reblogged this · 2 weeks ago -
 tatersgonnatate reblogged this · 2 weeks ago
tatersgonnatate reblogged this · 2 weeks ago -
 bardicinspiration-blog reblogged this · 2 weeks ago
bardicinspiration-blog reblogged this · 2 weeks ago -
 bardicinspiration-blog liked this · 2 weeks ago
bardicinspiration-blog liked this · 2 weeks ago -
 dreamercec reblogged this · 2 weeks ago
dreamercec reblogged this · 2 weeks ago -
 cabbagesnail20122 reblogged this · 2 weeks ago
cabbagesnail20122 reblogged this · 2 weeks ago -
 cabbagesnail20122 liked this · 2 weeks ago
cabbagesnail20122 liked this · 2 weeks ago -
 drpippiss reblogged this · 2 weeks ago
drpippiss reblogged this · 2 weeks ago -
 drpippiss liked this · 2 weeks ago
drpippiss liked this · 2 weeks ago